As your company grows and changes, maintaining security at all levels of the organization is even more critical. Neglecting your data access security can cause irreparable harm to your organization’s reputation and bottom line and lead to hefty financial penalties for SOX non-compliance.
As your company grows and changes, maintaining security at all levels of the organization is even more critical. Neglecting your data access security can cause irreparable harm to your organization’s reputation and bottom line and lead to hefty financial penalties for SOX non-compliance.
To remain SOX compliant, you must manage access rights during onboarding, role changes, and offboarding. You must also practice Segregation of Duties (SoD), which ensures that more than one person or department shares the responsibilities for key processes. For example, the person who requests an item for purchase is not the same person who approves the purchase. Further, the person who approves the purchase is not the same person who reconciles monthly accounting reports. SOX compliance also demands that you maintain an access control matrix, perform periodic access audits, and automate any reporting.
If your company has a centralized IT team with multiple manufacturing and distribution centers and multiple ERP production databases, your IT team can quickly become swamped with user security requests. If your company is experiencing the understaffing issues that many companies are grappling with, your IT members are constantly busy onboarding and offboarding, tightening/ untightening access for existing users, and unlocking incorrect passwords. Most importantly, your IT department must ensure all these requests are duly approved by management and executed accurately and expeditiously. In addition to many production QAD databases, there are TEST and other PLAY systems with user security requests that IT must maintain.
So, how do you manage all this without losing your mind?
32 Soft has designed a web application, the QAD User Security Management System (QUS), that makes quick work of the processes involved in keeping your data access secure. The QUS system is a single place where IT staff can manage ALL QAD user security requests across multiple production and test environments.
QUS features …
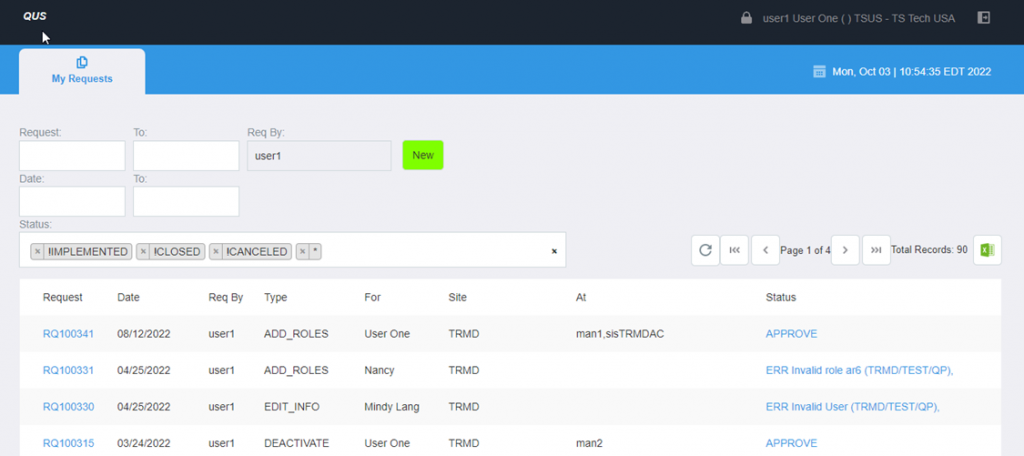
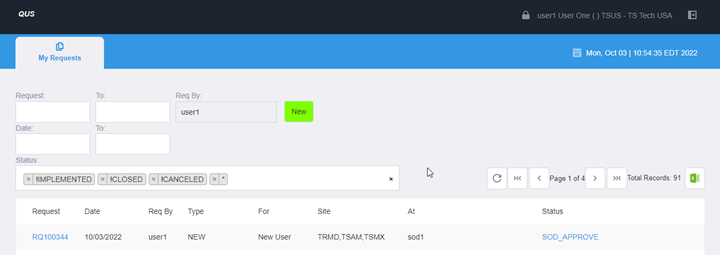
- A My Requests view where you can easily see all security requests and their status, sort and filter by status, and drill down to the original request.
- An approval flow. The user requests access for approval by a manager or functional approver. The manager receives an email with a link to an approval view. The request can also be automatically routed to local sites’ “functional” approver.
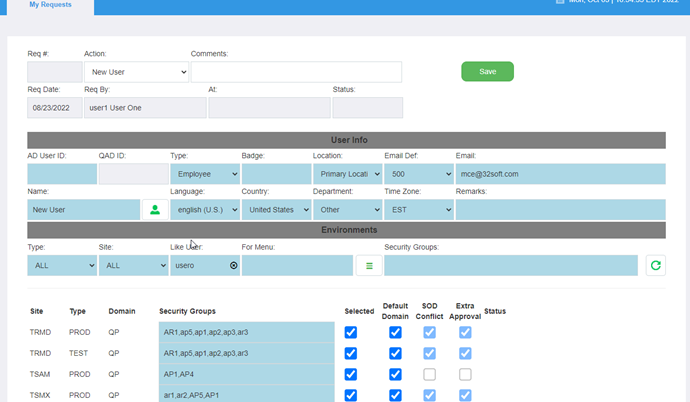
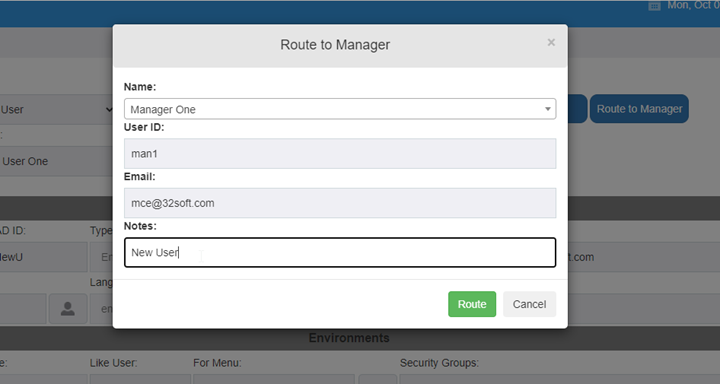
The manager receives an email with a link to an approval view. The request can also be automatically routed to local sites’ “functional” approver. Manager Approves
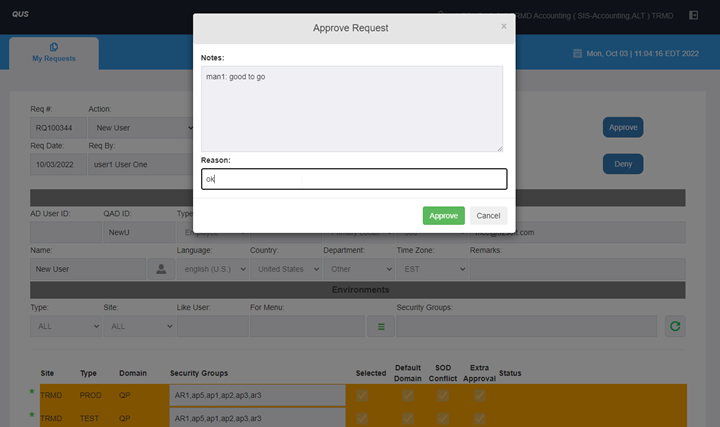
A check for SOD conflicts. If SOD is detected, it’s nicely shown on the screen that the request needs extra approval
Automatically routed to SOD (Segregation of Duties) approver. The plant manager receives an email with a link to approve.
- Implementation is automatic once the request is approved, which is a great time saver if you have multiple production and test sites.
- Built-in validation during implementation shows you the reason for errors and will stop the validation process so the errors can be corrected and the data submitted again.
One of our valued clients with 18 QAD Production environments and 20+ QAD test environments, launched QUS successfully at the end of 2021. The feedback we have received from the IT director and the entire IT team who use QUS daily to manage security requests has been positive. It continues to meet all its objectives.
If you’d like to know more about the QAD User Security Management System, you can contact us for a demo or, register now for our upcoming webinar, Managing QAD Access Security.